What does CISSP Domain-8 Focus on?
CISSP Domain-8 is focused on Software Development Security, and it contains 5 Sub-Objectives (Given Below). We will discuss the major concepts you must understand from exam perspective.
8.1 Understand and integrate security in the Software Development Life Cycle (SDLC)
This Objective focus on Security Integration into the Software Development Life Cycle (SDLC)
8.2 Identify and apply security controls in software development ecosystems
This CISSP Objective focuses on the common understanding of Development tools, Languages and Commuter Aided Software Engineering (CASE) covering various topics like Software Development Methodologies and integrating security into SDLC.
8.3 Assess the effectiveness of software security
This CISSP Objective focus on Software Risk assessments and Auditing
8.4 Assess security impact of acquired software
This Objective focuses on security integration in Software Acquisition process for Open source, Commercial-over-the-shelf (COTS) Software, third party Software, Managed and Cloud services
8.5 Define and apply secure coding guidelines and standards
This is by far highly testable topic in CISSP Exam, and it focuses on deep understanding of Software Development related vulnerabilities like SQL Injection, XXS, Cross-Site-request Forgery and other OWASP related vulnerabilities. Once you have the deep understanding of these vulnerabilities, as a security professional, you should think about how to enforce security practices during development through Secure Coding practices, Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Integrated Application Security Testing (IAST) into the Testing phase before release of the software in the production.
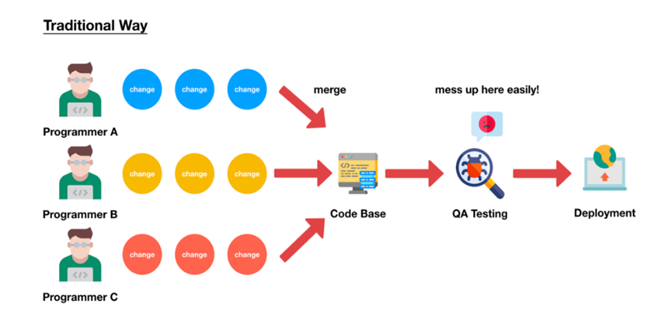
What are key Security Integrations in SDLC
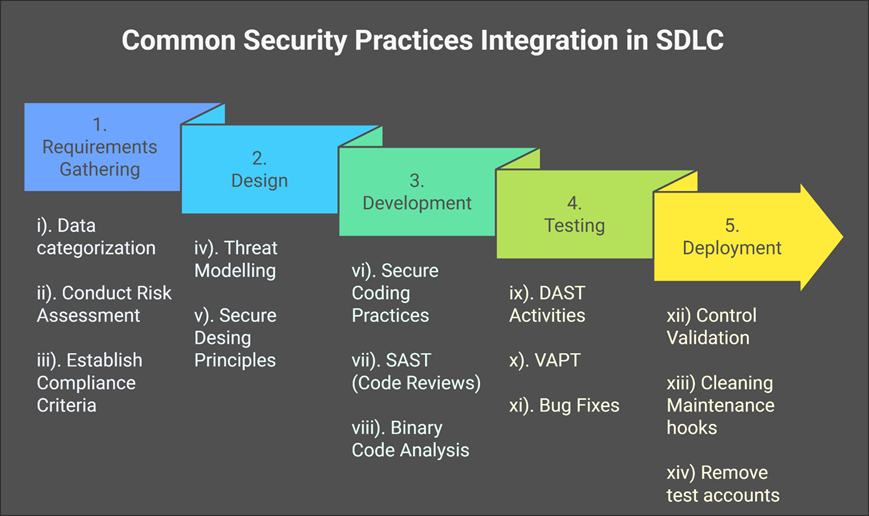
Application security is paramount as they process sensitive information; hence, security should NOT be an afterthought in Software Development. Software development Lifecycle is a structured project Management approach to developing software and applications. The table below indicates the security touchpoint in the SDLC. Security should be integrated in the very initial phase of SLDC and should not be a retrofit. The picture below Explains the various Security integration into the SDLC.
What are the various SDLC Methodologies?
The below Table is a short and crisp way to understand the various SDLC Methodologies.
|
Short description |
Pros |
Cons |
Best suitability |
|
|
Waterfall Model |
A linear and sequential approach with distinct phases.
Each phase must be completed before the next begins. |
Simple and easy to understand and use.
Clear milestones and structured process. |
Inflexible (rigid), especially with changes.
Late testing can lead to higher costs. |
Best for well-defined projects with minimal expected changes. |
|
Incremental Model |
Develops a system through repeated cycles (increments) and adds features in each increment.
Each increment is fully functional and can operate independently. |
More flexible than Waterfall.
Early releases for testing and feedback. |
Needs good planning and design.
This can lead to higher costs over time. |
Suitable for projects where functionality can be delivered in phases. |
|
Prototyping
|
Creates prototype (small model) before actual development.
|
Early feedback, and more user involvement.
|
This can lead to insufficient analysis.
|
Projects with unclear user requirements.
|
|
Spiral |
Combines design and prototyping in stages, emphasizing risk analysis.
Each cycle involves planning, risk analysis, engineering, and evaluation. |
Focus on risk assessment and reduction.
Highly flexible and adaptable. |
Complex and can be more costly.
Requires expertise in risk evaluation |
Ideal for high-risk projects requiring iterative risk assessment |
|
Joint Application Development (Jad) |
Brings together business stakeholders and developers in collaborative workshops.
Focuses on consensus and collaborative decision-making. |
Encourages stakeholder involvement and feedback.
Rapid development and delivery. |
Can be time-consuming.
Depends heavily on stakeholder commitment. |
Projects requiring extensive user interaction.
Projects where user requirements are a major factor. |
|
Rapid Application Development (RAD)
|
Emphasizes rapid development and iterations. |
Faster development reduces risk. |
Depends heavily on a strong team and user involvement. |
Small to medium projects with tight schedules. |
|
Cleanroom Model
|
Cleanroom focuses heavily on mathematical models to deliver defect-free software |
High quality, less error prone. |
Can be rigid and time-consuming. |
Focuses on defect prevention, ideal for critical systems needing high reliability |
What the Key Core Concepts for CISSP Exam?
Core Concepts
- Security should be integrated from the initial phase of the software development, aka the Move Left approach
- Security requirements should consider regulatory, and data protection needs and must be documented, approved, and disseminated.
- Apply principles like least privilege, defense-in-depth, and secure-by-design during the Design phase
- Ensure the chosen methodology aligns with team expertise and organizational culture
What is Agile Software Development
Agile is a flexible and adaptive approach to software development, emphasizing incremental progress and active collaboration. Unlike traditional methods, Agile focuses on delivering functional software in smaller, manageable parts, called iterations or sprints, which allows teams to adapt to changing requirements efficiently.
The core principles of Agile include prioritizing customer collaboration over rigid contracts, delivering working software frequently, embracing changes even late in the process, and fostering continuous communication within teams. Agile values simplicity, sustainable development, and self-organizing teams capable of delivering high-quality outcomes.
Several frameworks implement Agile principles, each suited for specific scenarios.
Scrum
Scrum is a widely used agile approach, featuring time-boxed sprints and roles like Scrum Master and Product Owner and the Scrum team. The product manager is accountable for clearly articulating the product vision and goals to align the team with business objectives. This role defines and validates the acceptance criteria for deliverables, while the Scrum Master is an updated avatar of the project management with key qualities like being iterative, adaptive, and customer-driven. This role is responsible for facilitating scrum events, coaching the team, removing any obstacles hindering team progress while fostering collaboration and helping the team remain focused on sprints. The Scrum Team works closely with the Product Owner and Scrum Master to ensure alignment with sprint goals
The other Popular Agile methodologies include
|
Kanban |
Kanban focuses on visualizing workflows and improving process efficiency |
|
Extreme Programming (XP) |
XP emphasizes technical excellence with practices like test-driven development (TDD) and pair programming. |
|
Learn Methodology |
Lean methodology focuses on minimizing waste (gaps), maximizing value, and facilitating faster delivery of products. |
|
Scaled Agile Framework (SAFe) |
Scaled Agile Framework (SAFe) is a structured approach for scaling Agile practices across large organizations. SAFe is a comprehensive framework to align multiple teams, stakeholders, and business goals while maintaining Agile principles. SAFe incorporates roles, events, and artifacts to manage complex, large-scale projects efficiently by aligning the business team with the technical teams toward shared goals. The SAFe framework emphasizes lean thinking and continuous delivery. I recommend you visit the Scaled Agile Framework to get a practical feel of the framework. |
Agile methodology makes it ideal for dynamic environments, including cybersecurity projects, where rapid responses to threats are essential. It ensures a balance between speed and quality, allowing organizations to meet evolving needs while maintaining robust security practices throughout the development lifecycle.
What is the difference between DevOps & DevSecOps?
DevOps is a cultural and technical approach that combines development (Dev) and operations (Ops) teams to improve collaboration, streamline workflows, and deliver software faster and more reliably. It emphasizes automation, continuous integration/continuous delivery (CI/CD), and infrastructure as code (IaC) to reduce development cycles and enhance efficiency. Key tools include Jenkins, Docker, and Kubernetes.
DevSecOps extends DevOps by integrating security practices into every phase of the development lifecycle. It ensures security is a shared responsibility, not an afterthought. Automated security testing, vulnerability scanning, and compliance checks are embedded into CI/CD pipelines to deliver secure software without slowing development. The figure shows the various security activities and tools used in different phases in DevSecOps.
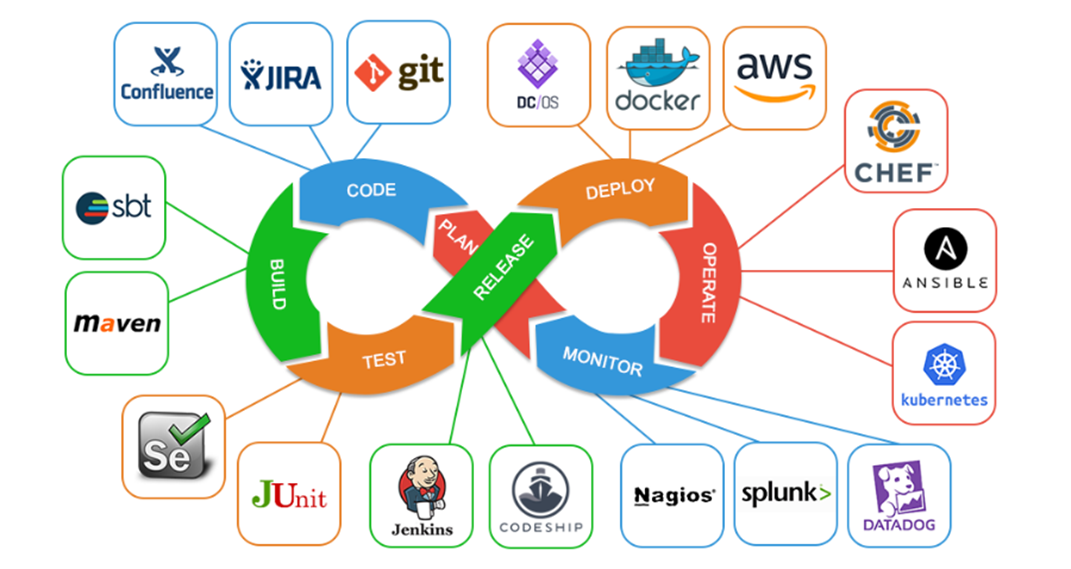
Continuous Integration and Continuous Delivery (CI/CD)
|
|
|
CI/CD stands for Continuous Integration and Continuous Delivery/Deployment. CI/CD helps streamline the development process, ensuring high-quality software is delivered rapidly and efficiently. CI involves the practice of automatically integrating code changes into a shared repository multiple times a day. Each integration is verified by automated tests to detect errors early, while CD is the practice of automatically preparing code changes for production release. After the code passes tests and is integrated, it’s made ready for deployment to production, ensuring it can be delivered at any time with minimal manual intervention.
|
What are Various Maturity Models in SDLC?
Leadership conducts maturity model assessments in SDLC to evaluate the effectiveness and efficiency of an organization's software development processes. This provides a structured approach to identify strengths, weaknesses, and areas for improvement. Maturity assessments are important for organizations to align their practices with industry standards, optimize workflows, reduce risks, and enhance overall quality. Typically, All Maturity domains have few things in common.
Here are some of the Software maturity assessment models you should know as a CISSP.
|
Developed by |
Core Focus Domain |
Maturity Criteria |
Maturity Levels |
|
|
Capability Maturity Model Integration (CMMI) |
Software Engineering Institute (SEI) at Carnegie Mellon University |
Process improvement in software engineering and organizational development |
Process performance, capability, and improvement |
5 Levels: Initial, Managed, Defined, Quantitatively Managed, Optimizing |
|
Software Assurance Maturity Model (SAMM) |
OWASP |
Software security assurance |
Software security practices |
3 Levels: Initial, Repeatable, Defined |
|
Building Security in Maturity Model (BSIMM) |
Synopsys (created independently) |
Software security practices in real-world software development environments |
Descriptive model based on real-world data |
3 Levels: Basic, Deployed, Advanced |
What is Software Change Management?
We have already discussed the change management process in Domain-7. Change management has great significance in the entire Software Development Lifecycle to avoid surprises and downtimes. The change management process should be followed as and when there are modifications to the software requirements, software design, modifications to the code base, bug fixes, configuration changes, and updating of external libraries or packages. Any new legal or regulatory requirements should also be taken through the change management process.
What is Software Configuration Management?
Software Configuration Management (SCM) is the process of ensuring that the software configuration is consistent with the security baseline and that any changes to the configurations are tracked well. From an implementation perspective, it is important that the organization establish the capability to identify the Configuration Items (CI) pertaining to the software and systematically control the configuration. It is also important to keep track of all configuration changes and audit the configuration to ensure integrity and correctness.
SCM activities include version control, change management, and release management. It is recommended that the organization implement automated tools for version control, documentation, and reviews.
What is Integrated product Team?
An Integrated Product Team (IPT) in the software lifecycle is a cross-functional team responsible for the development, integration, and delivery of a product. The IPT collaborates throughout the entire software development process, ensuring that all aspects, from planning to maintenance, are aligned with product goals and quality standards. The IPT consists of stakeholders from different teams like Product owners, managers, developers, Quality Assurance, Security, UI/UX designers, operations, Business analysts, and SMEs to ensure all decisions are reviewed from different perspectives during the software lifecycle.
What is the difference between Markup and Scripting Languages?
We use Markup and scripting languages, especially for the front-end interface of applications. Since an HTML page is parsed on the user machine by the browser, we need to understand the security challenges related to the use of these languages.
|
HTML |
HTML is a standard markup language for creating and structuring web pages and web applications. These languages may be susceptible to Cross-site scripting (XSS) and malicious file uploads. It is recommended to sanitize and validate user input and use a Content Security Policy (CSP). Content Security Policy (CSP)CSP is a security standard designed to protect web applications from various types of attacks, such as Cross-Site Scripting (XSS), data injection, and clickjacking. It helps developers define a set of rules that specify which sources of content are considered trustworthy. This mitigates the risk of malicious scripts being executed within the browser CSP can enhance security by limiting JavaScript execution to only scripts hosted on the developer's domain, preventing inline script tags to reduce injection attacks, and also including a report-URI directive to mandate browsers to send reports when a violation happens. |
|
CSS |
CSS is a style sheet language used for describing the presentation of a document written in HTML or XML. CSS can also be susceptible to Cross-site scripting (XSS) via style injection and clickjacking attacks and hence it is important to validate and sanitize all inputs and use secure Content Security Policy (CSP) settings. |
|
JavaScript |
JavaScript is a scripting language for creating dynamic and interactive content on web pages and providing additional functionalities. While JavaScripts are heavily used, they might also be susceptible to Cross-site scripting (XSS), Cross-site request forgery (CSRF), and Code injection. It is recommended to sanitize user input, Use CSP and Sub resource Integrity, and Implement proper error handling. |
|
Python |
Python is a high-level, interpreted programming language with dynamic semantics, used for web development, scripting, data analysis, and more. The code may be susceptible to code injection, command injection, and Cross-site scripting (XSS) when used in web applications and hence it is important to validate and sanitize user input, Use secure coding practices, Implement access control and authentication mechanisms. |
What is Software Runtime?
A software runtime is a virtual space where a program or application executes. This environment provides the necessary services and resources for the program to run, such as memory allocation, thread management, and handling external inputs or outputs. The runtime acts as an intermediary between the application and the underlying operating system and hardware. It is very important that software is executed in a secure runtime. Here is a table containing the secure runtime components and the security considerations:
What are various Development Toolset?
Developers use a variety of toolsets to develop the code. You should be familiar with the purpose and security capabilities of these modern-day tools (hopefully you are using the latest versions) to leverage them as per security best practices.
|
Libraries |
Libraries provide reusable routines or functionalities to simplify software development. Libraries often include security-focused functions and routines. Outdated, insecure, and external libraries, if not properly managed may lead to compromise and supply chain risks. From a security perspective ensure we use libraries from reputable sources only and keep them updated to address security vulnerabilities. While using a third-party library, ensure we conduct a dependency check using tools like OWASP Dependency-check, npm, etc., ensure their integrity is intact by validating the checksum or signed release and scanning them for vulnerability before integrating them. If some Libraries require licensing terms, validate licensing as per the organization's licensing policy and try to automate the checks using appropriate tools like FOSSA, Sonatype Nexus, etc. |
|
Integrated Development Environments (IDE) |
IDE is a software that provides an interface and features for developers to facilitate writing, editing, and managing source code. Modern IDEs come with integrated features like code analysis, secure coding standards, and version control integration. It is important to use feature-rich IDEs for development in an isolated environment and keep them updated with the latest versions, plugins, and extensions. Integrated features to detect vulnerabilities during coding should be enabled to facilitate secure coding. |
|
Debuggers and bug databases |
Identify and resolve software bugs, manage bug reports, and track debugging efforts. Help in identifying security vulnerabilities in code; bug databases can track security-related bugs. |
|
Compilers |
Compilers translate source code into executable programs, optimize code, and check for syntax errors. Use compilers that offer security features like buffer overflow protection and code sanitization. |
|
Testing tools |
Developers use a lot of testing tools to automate the process of verifying and validating that a software program or application meets its requirements. The security team gets involved in validating the test cases for effective security. |
What is a Code Repository?
Code repositories serve as a central storage location where source code, files, and related assets are stored, managed, and version controlled. It encourages collaboration and contributions among developers as they use code repositories to collaborate, track changes, and maintain a history of their work and integrates features like Code reviews, code scanning, and integration with CI/CD pipeline to automate build, test, and deploy the code.
Many times, the teams may use public (accessible to everyone) or private (restricted access) repositories for storing and managing the code. These repositories are commonly hosted on platforms like GitHub, GitLab, Bitbucket, or even self-hosted solutions dedicated to the company.
Software code is intellectual property and hence these repositories hosting the code should be protected with strong Role Based Access Control (RBAC) and MFA. Avoid storing sensitive data (e.g., API keys, passwords) in the repository and perform periodic scans to conform with the practice. Finally, ensure any third-party integration with the repository is appropriately tested.
Often access control, encryption for data at rest and in transit, and integration with security tools.
What are various Software Testing techniques?
What is a Code Repository?
Code repositories serve as a central storage location where source code, files, and related assets are stored, managed, and version controlled. It encourages collaboration and contributions among developers as they use code repositories to collaborate, track changes, and maintain a history of their work and integrates features like Code reviews, code scanning, and integration with CI/CD pipeline to automate build, test, and deploy the code.
Many times, the teams may use public (accessible to everyone) or private (restricted access) repositories for storing and managing the code. These repositories are commonly hosted on platforms like GitHub, GitLab, Bitbucket, or even self-hosted solutions dedicated to the company.
Software code is intellectual property and hence these repositories hosting the code should be protected with strong Role Based Access Control (RBAC) and MFA. Avoid storing sensitive data (e.g., API keys, passwords) in the repository and perform periodic scans to conform with the practice. Finally, ensure any third-party integration with the repository is appropriately tested.
Often access control, encryption for data at rest and in transit, and integration with security tools.
You must be familiar with the following types of testing performed during software development. Let's understand a bit more about these.
|
SAST (Static Application Security Testing) |
SAST is performed to analyze source code or compiled versions of code to find security flaws when the code is static without running the program. The various methods used for SAST are as follows: · Manual Code reviews and Peer code reviews · Automated Static Analysis Tools involve scanning the source code or binaries to detect vulnerabilities automatically. · IDE plugins highlight the potential vulnerabilities while the developers write the code. · Integrating SAST tools into the CI/CD pipeline during the build phase. · Usage of custom scripts
The PRIMARY advantage of SAST is that it can detect issues early in the development cycle and can identify the following types of vulnerabilities. · Code level vulnerabilities like buffer overflows, SQL injection, and hardcoding secrets (passwords and API keys) · Validation of secure coding practices · Analyze Data flow issues like potential leaks or misuse · Dependency analysis on third-party libraries for known vulnerabilities · Identity any logical flow errors like race conditions, insecure loops · Identity any hardcoded secrets in the code · Validating adherence to specific code-level requirements to industry regulations like PCI-DSS, HIPAA, or GDPR.
The downside of SAST is that it cannot identify runtime issues and often requires expert analysis. |
|
SCA (Software Composition Analysis) |
Software Composition Analysis (SCA) is the process of identifying and managing the Third-party and open-source components, libraries, and dependencies used within a software application. It focuses on analyzing these components for security vulnerabilities, licensing compliance issues, and outdated versions by comparing detected components against vulnerability databases (e.g., NVD, OSS Index) and license databases. SCA can be integrated into development workflows. SCA can be performed during development, build, before deployment and also when the application is in production.
|
|
DAST (Dynamic Application Security Testing) |
DAST involves testing an application during runtime to find vulnerabilities that are only detectable when a program is running. DAST tools interact with the application as a black-box tester and simulate the actions of an attacker to uncover security issues in real time. The various methodologies used for DAST may include: Crawling: to crawl the webpages or application modules to identify exposed attack surfaces like forms, API, URLs Fuzzing: inputting malformed data to see the security behavior of the application. Authentication Testing: checks for attacks like brute force, session hijacking, or credential stuffing.
DAST can identify a wide range of vulnerabilities in the application which may include Injection flaws like SQL Injection, command injection, Cross-site Scripting (XSS), Broken authentication, Security misconfigurations, Sensitive data exposure, CSRF, and server-side issues. |
|
IAST (Interactive Application Security Testing) |
IAST combines aspects of both SAST and DAST by testing applications from within using instrumentation during runtime. It provides the benefits of both SAST and DAST, offers more accurate results, and reduces false positives. IAST is getting more popular now as the IAST tools can be seamlessly integrated into DevSecOps CI/CD pipelines (automation) to provide real-time security feedback during testing. IAST is also suitable for applications where both source code and live running are accessible and continuous testing is needed. |
|
Canary Testing |
It is an approach in which any new software version is first released to a small subset of users. This small subset of users or servers is called a canary and once the version is rolled out to this subject, it is closely monitored for behavior (feedback) and performance. In layman’s language before deploying any changes, we test it out in a pilot phase. The whole idea is to test the stability and functionality of the new version in a production environment with real users but on a limited scale. Canary Deployment: Canary deployments extend the idea of canary testing to the deployment process. Any new software version is deployed first to a small subset of users before any large-scale deployment. |
What are various environments in Software Development Lifecycle?
The software lifecycle involves multiple environments as given below:
|
Development environment |
This is the setup where the developers write and test codes, build new features, fix bugs and experiment any new ideas. Security recommendations · Development infrastructure should be separated from production and the developer's access to production data should be restricted. · It is recommended for developers to have separate accounts for development and production where the production accounts are strictly controlled with the least privileges as per role-based access controls. · The development environment should not have access to any production data. · All development accounts should be removed from the product before pushing to the test environment.
|
|
Test environment |
The test environment is for quality assurance personnel who need to validate the functionality, performance, and reliability of the software before it moves to production. It is often a replica of the production environment. Security recommendations · Ensure the test environment is separated from development and production. · Do not use live production data for testing as production data may contain sensitive information like PII. If there is a pressing need, make sure to sanitize or anonymize production data before usage in testing. · Access should be limited to the QA team |
|
Staging |
This is the environment where the software is finally run to mimic the production environment (like a lab). Staging mirrors the production environment but remains isolated with no direct production dependencies. Security recommendations · The testing must be performed with dummy accounts and not real production accounts · All integration with real production applications and api should be disabled. |
|
Production |
This environment runs on a secure and hardened infrastructure and must be separated from the dev/test/staging environment. Any sensitive data should be encrypted, and access is restricted to only essential personnel. |
What are security considerations during Software Acquisition?
When a firm requires software to meet its business objectives, there are two approaches an organization can take. The first preference will be to develop the software in-house for more control which means the organization gains direct evidence of security controls in place throughout the SDLC. However, due to lack of funds/lack of technical expertise or based on Cost-benefit analysis, the organization may decide to look out for a third party providing software or services.
Security Considerations during Acquisitions of Commercial Off-The-Shelf (COTS)· The term refers to ready-made software purchased from vendors and used as-is. This approach is good when the organization has standard requirements and may not need customized features. The advantage of COTS is that the functionality can easily be verified or confirmed by the vendor. Often these software are verified by independent parties (certifications) and software updates are readily available, however, we should be aware of the risks involved with COTS; these are: · Inability to validate code-level vulnerabilities: Since the software is provided by a third party and acts as a black box for the user (no internal code visibility), the organization does not have the accessibility to perform SAST on the source code. COTS may be more often subject to Common vulnerabilities like Privilege escalation, Buffer overflow, etc. · There are chances that the vendor may go out of business which might impact the company operations. It is advisable to assess such risk and if the possibility is deemed high, Code escrow services can be taken up with mutual agreement. Code Escrow is the secure storage of a software source code with an Independent third party and the code is released to the licensee under specific agreed-upon conditions like vendor going out of business or bankrupt. The organization should maintain an accurate inventory of COTS software and components and track their licenses. Organizations must integrate Risk Management Practices for COTS and evaluate risk periodically through activities like threat modeling, vulnerability assessment, and pen testing. A thorough risk assessment on the architecture and related vulnerabilities should be performed. Finally, as Static Application Security Testing (SAST) is not an option in COTS, try implementing additional controls like IDS/IPS, WAF, or compensating controls to keep the risk within acceptable limits.
|
Security Considerations during Acquisitions of Open-source software (OSS)The Organization leverages software with source code that is freely available for modification and distribution. This approach may reduce costs but requires careful management of security and compliance aspects. Here are a few risk related to OSS: Copyleft Issues: Many OSS are free to be used, modified, and distributed for individual and commercial use, however, as a CISSP you must clearly understand the licensing term in consultation with the legal team before integrating open-source code or modules in the commercial software, as few OSS agreement requires the source code to be made freely available. Technical Skills: OSS can be complex to use and require high technical skills for usage. Ensure your team understands the solution better and has the required technical skills. Support and Updates: In some cases, OSS may lack dedicated support and timely patches as such projects are mostly run through donations. Ensure you perform a sufficient evaluation before starting to leverage such software. Validate Sour Code Integrity: Since OSS code is available equally to good and bad guys. Bad Guys can insert malicious code and package them, Ensure to download OSS from official repositories after appropriate code validation. |
Security Considerations during Acquisitions of Third-Party SoftwareIn this approach, the Organization outsources the software developed to an external entity. This approach offers the required customization but relies on a third party for updates, security, and support. Selection of third party should be based on specific skill set and expertise. The agreements with the Third party should take care of secure coding aspects like the manual code review can be performed by the third party and company in-house developers. Another approach can be to make sure the product is certified by an independent third party of assurance. |
Security Considerations during Acquisitions of Managed ServicesMany companies outsource their IT and security infrastructure to be managed by a third party so that the business can focus on their core expertise. In such cases, the managed service providers may use their software or integrate existing software with their software through secure APIs. Managed services often include security monitoring, network monitoring, technical support, help desk, and so on. It may include services like cloud-based solutions where the provider is responsible for the software's operation, maintenance, and security. Timely and periodic validation of the managed service provider security posture and practices is important which may include reviewing their compliance audit reports for SOC2 type 2, CSA Star Audit reports, and so on. |
Security Considerations during Acquisitions of Cloud Services
Availing cloud services is very common in this day and age as it provides almost negligible cost on Capital expenditure (CapEx) and the company has to pay as use. Scalability is a key driver, as cloud services allow organizations to seamlessly adjust resources to meet changing demands, whether scaling up during peak times or scaling down to reduce costs. The on-demand self-service feature empowers businesses to access and manage resources instantly without lengthy procurement cycles. The global reach and broad network access of cloud platforms enable organizations to deliver services to users anywhere, enhancing customer experiences and operational agility. Additionally, reliability and resilience offered through redundancy and disaster recovery solutions ensure business continuity. With automated updates, strong security protocols, and compliance certifications, cloud services help businesses stay secure and compliant while focusing on their core objectives.
What are various Code level Vulnerabilities?
Due to poor coding practices and lack of appropriate testing, the vulnerabilities at the source-code level can impact the overall security of the data being processed by the application. Here is a concise summary you need to know from CISSP Exam perspective. Pay special attention to the root cause and top mitigation:
SQL VulnerabilityIf an application lacks input validation, an attacker can inject malicious input to manipulate the backend SQL query to access or modify the database data. Example: Injecting ' OR '1'='1'-- into a login form to bypass authentication In this case, the application is not validating or sanitizing the highlighted data above due to which the SQL query gets dynamically generated to bypass authentication. SQL Injection may lead to loss of confidentiality, and authentication bypass, and the attacker can read and modify database information. 1. Use of Parametrized Queries can ensure that user input is treated as data, not executable SQL. Example: SELECT * FROM users WHERE username =? AND password = ?; 2. Implement strict input validation and sanitization on the frontend application 3. Use of prepared statements – it’s a specific implementation of a parametrized query in which the query is precompiled and stored by the database |
||||||||||||||||||||||||||||||||||||||||||||||||
|
What is API Security?
API is a collection of rules, protocols, and tools to provide an interface for an application to communicate with other applications or processes. This provides an abstract system that developers can leverage directly without understanding the internal workings of the API. We use API almost everywhere. Some of the forms of API in use are:
|
Library/Framework API |
These are pre-written programming APIs built in the software library which developers can use to develop software applications. |
|
Operating system API |
These are pre-written APIs available as part of the Operating System (OS) which facilitate the interaction of various applications with the underlying Operating System |
|
Web API |
These are APIs used for building and interacting with Web-based services running on different devices and Platforms (OS) |
Simple Object Access Protocol (SOAP) API
SOAP API is used to exchange structured information in web services, using XML, HTTP, or SMTP. It uses XML for messaging and data exchange and mostly relies on HTTP protocol for transport but can also be used for SMTP and other protocols.
Security Aspect of SOAP API:
SOAP is a strict standard and ensures a high level of consistency. By strict it means a built-in error handling mechanism. SOAP APIs have built-in security features through WS-Security for end-to-end encryption and support SSL/TLS for transport-level security.
SOAP supports more complex security configurations compared to REST. The downside is, that SOAP APIs have higher processing overhead due to extensive security standards making them slower than RESTful APIs.
SOAP API is still heavily used for complex operations and enterprise-level applications.
Representational State Transfer (REST)ful API
RESTful is not an API itself but an Architecture Style for building stateless web services using HTTP. It emphasizes simplicity and scalability to build lightweight, maintainable, and scalable web application APIs. RESTful API uses flexible data formats (JSON, XML, etc.). RESTful, which means Representational State Transfer, primarily uses HTTP/HTTPS for communication and data can be transmitted in various formats such as JSON, XML, or plain text. APIs built on RESTful approach are Lightweight and faster than SOAP. It allows interaction with a web-based system via simplified URLs. Due to its simplicity of implementation, RESTful Framework is easier to understand and implement.
Security Aspect:
While RESTful APIs provide better performance and scalability, they require explicit implementation of security measures at the application layer. This API relies on HTTPS for encryption. Token-based authentication (like OAuth) needs to be implemented for secure access. As Oauth mostly use JSON tokens, these APIs are faster than SOAP APIs and that’s the reason they are getting more popular.
These are more suitable for web and mobile applications.
API Authentication
Authentication in API is critical for the security of communication, here are the various options available, with a security Rating.
|
Authentication option |
Details |
|
No authentication / based on a custom token |
Only acceptable for completely open, read-only APIs with no sensitive data involved. |
|
Basic authentication (based on username /password or API key) |
Easy to implement but not very secure on its own. There is a Security risk if credentials/API keys are intercepted. This approach is often used with other methods like HTTPS. |
|
SAML (security assertion markup language) |
Enterprise-focused, for single sign-on (SSO), however, it can be complex to implement. |
|
HMAC (hash-based message authentication) |
Provides message integrity and signature, However, the keys must be handled securely. |
|
Oauth 2.0 |
A secure and widely adopted standard that provides fine-grained access control. |
What are various Secure Coding Practices?
Secure coding guidelines should be set up to ensure developers follow these guidelines while developing software applications. These established practices can be generic along with language specific to address issues. OWASP, CERT Secure Coding Standards, and ISO 27034 (Application Security) provide good guidance on how to establish Secure Coding practices in the company.
Here are some Secure Coding practices as per OWASP guidelines:
|
Input Validation |
Assume all inputs from users as untrusted and implement client-side and server-side input validation. It is important to implement server-side validation as the client's side input validation can be circumvented by the attacker through disabling the validation script or modifying the data after validation (data diddling) before it is sent to the server. |
|
Output Encoding |
Encoding output refers to the process of converting potentially harmful characters within data before it's displayed on a webpage or sent to other systems. Encoding the output ensures that any harmful data injected by the attacker in the input field is rendered harmless preventing them from getting executed resulting in the prevention of Cross-Site scripting (XSS). E.g. Special characters like <, >, ', and " are replaced with their HTML entities (e.g., <, >, ', "). |
|
Access Controls |
Implement robust authentication like Multi-Factor Authentication to verify user identity and ensure authorization is based on the least privilege principle. |
|
Error Handling |
While error messages help in troubleshooting, errors displaying internal information of the software can provide internal insights to the attacker leading to attacks. Play a balancing role so that the error does not reveal sensitive information to the attackers about the internal structure of the application. |
|
Session Management |
Use secure cookies with parameters like HttpOnly, Secure, and SameSite=Strict, proper session timeouts, and other measures to protect session data. |
|
Data protection |
Use encryption, tokenization, and access controls to protect sensitive data. Use strong cryptographic ciphers and protocols to ensure the security of data at rest or in transmission. |
|
Secure Configuration |
Securely configure the application and its environment, including the web server, database server, and operating system |
|
File Upload |
Ensure the file upload feature only allows the specific file format, else attackers can upload web shells to take control of the systems. |
|
Memory Management |
If an application ingests more data than it is designed for, it may lead to a buffer overflow attack. Ensure to follow good memory management practices. |
|
Coupling |
Coupling is the degree of dependency between different modules or components. This is due to various modules sharing data structures unnecessarily, which should be avoided. It would be preferred to keep the Coupling LOW to prevent difficulty in maintaining, test, and scaling the software. |
|
Cohesion |
Cohesion is the degree to which the elements within a single module are related and work together. A software developer should maximize the internal relationship within a module to make it self-contained and ready to be reused. Hence, HIGH Coupling is preferred. |